💻 mpc.is 📱
Multi-Party Computation (MPC) is a subfield of cryptography that focuses on enabling multiple parties to jointly compute a function over their inputs while keeping those inputs private.
In other words, MPC allows for computations on encrypted data without ever decrypting it. This means that multiple parties can collaboratively process data without ever revealing their individual inputs to each other.
Within the context of the crypto ecosystem, MPC is being used for two particular reasons: Distributed Key Generation (DKG) and Threshold Signature Schemes (TSS).
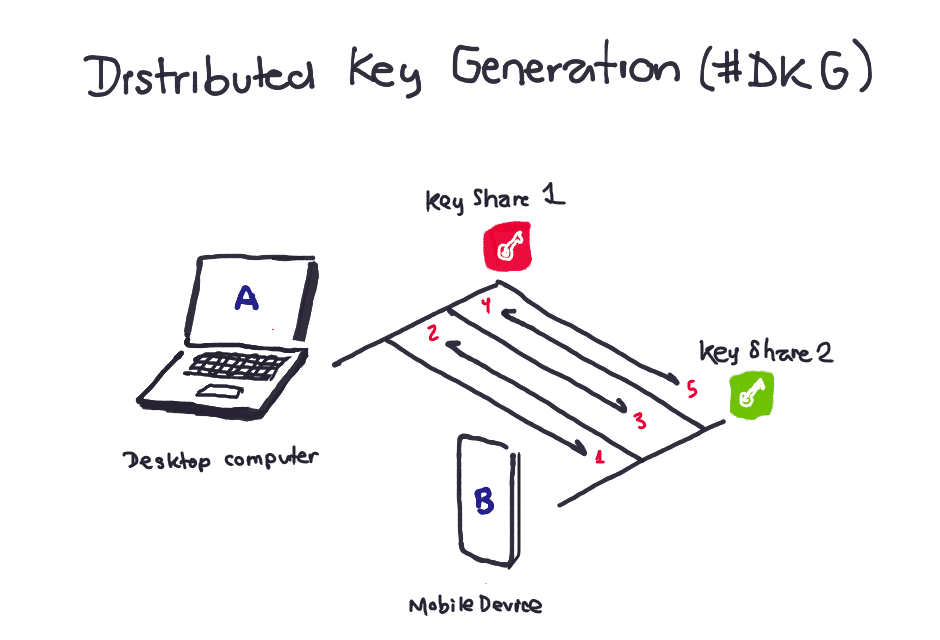
Distributed Key Generation (or DKG) is a protocol that enables multiple parties to collaboratively generate a public-private key pair. The catch here is that the private key is never assembled in its entirety at any single location or by any single party. Instead, each participant gets a share of the private key. Collectively, these shares represent the private key, but individually, they reveal nothing about the key itself. it enables the management of digital asset addresses the ability to sign transactions without having to rely on a single point of failure.
Threshold Signature Schemes (or TSS) extend the concept of DKG. Once the key shares are distributed amongst participants using DKG, TSS allows a subset of these participants (at least a certain threshold number) to collaboratively sign a document or a transaction. The beauty of TSS is that even though the signatures are produced collectively, the resulting signature is indistinguishable from a signature produced by a traditional single-party scheme. Moreover, unless the threshold number of participants agree to sign, no valid signature can be produced.

To showcase both processes, we have a live demo which relies on a Paillier cryptosystem to generate a 2-out-2 threshold signature schema using a computer and a mobile phone. We'll use the computer to kickstart the distributed generated key algorithm, and the phone to start the exchange of cryptographic data to eventually derive a crypto account and sign valid transactions for the account.
Scan this with your mobile phone to go to the mobile (📱) section. Upon scanning this, we'll redirect you to the computer (💻) section. Alternatively, click the QR code to copy the URL and open in a separate tab to mimic a separate device.